This is a follow up to our blog post titled, “QueBIT Blog - WARNING: TM1 may STOP WORKING on November 24, 2016.”
This blog takes a critical look at all of the available solutions to solve the upcoming TM1 SSL expiration issue. It also provides a way to find the best solution for your TM1 system, as well as methods to test the solution was successful.
For more information on QueBit TM1 services see:
Options based on your TM1 Version
The options you have are limited by your TM1 version. The infographic below shows the options by version.
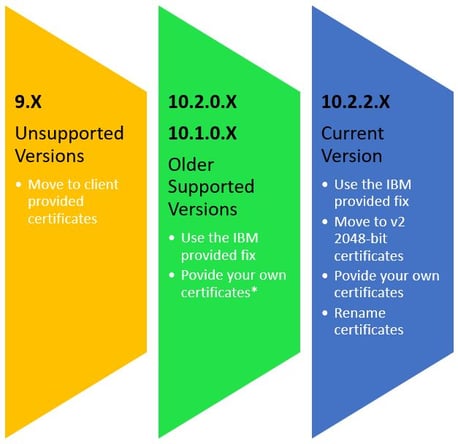

Options by TM1 Client Connectivity
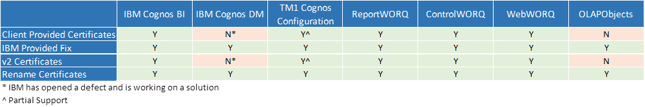
Technical Notes on TM1 from IBM
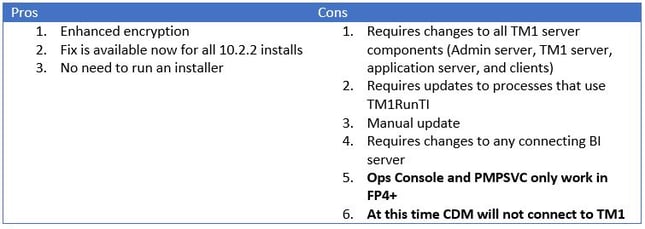
Using the IBM Provided Fix
IBM is working on an update for all supported versions of TM1. This update is not yet available, but is coming soon. The update will replace the existing 1024 bit certificates. IBM has issued the following tech-note http://www-01.ibm.com/support/docview.wss?uid=swg21990588
Users of Cognos Express: A fix for Cognos Express (which bundles with TM1) will also be made available. Depending on the version of Cognos Express, a manual approach (which will be documented) may be required.

Move to v2 2048-bit certificates
All installs of TM1 10.2.2 ship with 2048 bit certificates as well as the default 1024 bit certificates. To change to the 2048 bit certificates, follow the steps in this tech-note:
http://www-01.ibm.com/support/docview.wss?uid=swg21697266
To continue using TM1Top you must add the admin server ssl ca to the tm1top.ini configuration file. For example: adminsvrsslcertauthority=C:\Program Files\ibm\cognos\tm1_64\bin\ssl\tm1ca_v2.pem. (Do not put the path in quotes) You must also ensure that the TM1Top SSL folder is a copy of the TM1 Server SSL directory.
If BI is connected to TM1 the TM1 certificate information needs to be updated on the BI server. You can find details in this tech note. http://www-01.ibm.com/support/docview.wss?uid=swg21644290. The solution requires access to copy files from TM1 server to the BI server, as well as file edit permissions on the BI server.
Users of Cognos Express: This is not supported for Cognos Express versions prior to 10.2.2 (enterprise based installs)
Enabling WebWORQ to use v2 Certificates
Step 1: Locate the SSL directory
If your WebWORQ and TM1 Server share the same machine locate the TM1 SSL directory,
<TM1 Install Dir>/tm1_64/bin64/ssl
If WebWORQ is hosted on a separate machine the SSL directory should be in a similar location. If the SSL directory is not there, you can copy it from your TM1 Server
Step 2: Edit the web.config file
You can find the web.config file in the root directory of your WebWORQ site. A sample one is located in the WebWORQ install directory ( \Program Files\QueBIT\FrameWORQ\WebWORQ\Web). Open the file in the text editor of your choice, I prefer notepad++ but notepad works as well.
Locate the section that pertains to SSL Communication, it should look like this:
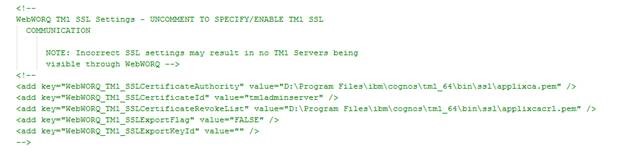
Remove the XML comment tags, “<!—“ and “-->”, around the “add key” portion so it looks like this.
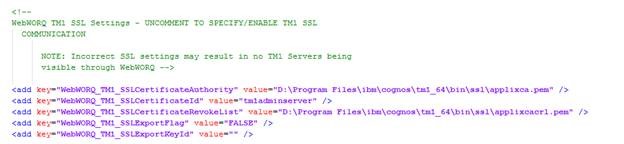
Update the file paths to point to the new certificates.
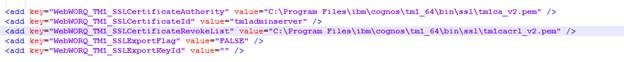
Step 3: Save and Test
Save the changes to the web.config file, this will trigger a restart of IIS. You can now test WebWORQ to make sure it can connect to TM1.
Provide your own certificates
Though a standard TM1 installation is configured to use SSL by relying on the certificates installed in the TM1_install_dir\bin\SSL directory, you could use your own certificates to maximize security. This process can be very complicated and requires knowledge of encryption technologies like OpenSSL. Instructions can be found here:
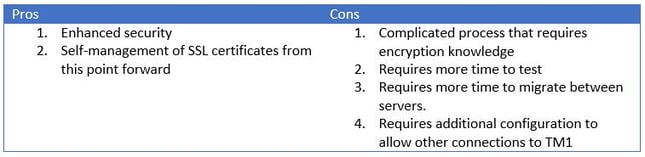
Users of Cognos Express: This is not supported for Cognos Express versions prior to 10.2.2 (enterprise based installs)
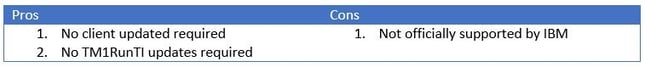
Rename certificates
Use the v2 (2048 bit) certificates by renaming them to match the v1 names. We have tested the approach and it works. Note this method is not officially supported by IBM
Step 1: Backup
Take note of all of your SSL directories and back them up by making a copy and renaming them ssl-bak
- Install/bin/ssl
- Install/bin64/ssl
- Client Install/bin/ssl
- Client Install/bin64/ssl
- Remote TM1Top Directory
Step 2: Create a sample SSL directory
In one of the ssl directories delete for following files:
- applixca.pem
- applixcacrl.pem
- tm1admsvrcert.pem
- tm1svrcert.pem
Rename the following files
- tm1ca_v2.pem change to applixca.pem
- tm1cacrl_v2.pem change to applixcacrl.pem
- tm1admsvrvert_v2.pem change to tm1admsvrcert_v2.pem
- tm1svrcert_v2.pem change to tm1svrcert.pem
Step 3: Copy SSL Files
Replace all SSL directories noted in step 1 with the directory created in step 4
Step 4: Test
Test that perspectives, architect, and TM1Top can continue to connect
Users of Cognos Express: This is not supported for Cognos Express versions prior to 10.2.2 (enterprise based installs)
Deciding What is Right for You
With so many different options it is important to understand which one fits your system best. We invite you visit our TM1 SSL Decision Assistance website.
Testing Your Solution
Once the fixes are in place there are few ways to test if the changes were successful.
- Review the admin server log: <install dir>/tm1_64/bin64/tm1admsrv.log look for the certificate authority in the server registration
- Review the TM1Server.log for SSL Settings
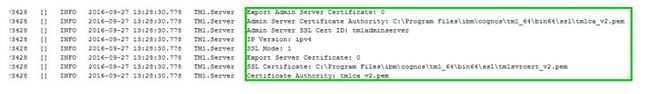
- Turn your system clock forward past the expiration date (11/24/2016). Only do this on a non-production system. Please be aware of governance and compliance rules regarding tests like this.
